Handshake, a decentralized naming protocol, utilizes the Merkle tree algorithm to achieve secure and efficient management of domain ownership and certificates. Let’s dive into the details:
- Background:
- The foundation of the internet’s security has traditionally relied on trusted Certificate Authorities (CAs). These CAs attest that a user is connecting to the correct server or node.
- However, this centralized model poses risks, as it relies on a handful of trusted actors, many of whom are for-profit corporations. If any of these trusted CAs fail, the entire security of the internet is compromised.
- Handshake’s Goal:
- Handshake aims to replace centralized trusted internet infrastructure with a decentralized Certificate Authority and a globally unique namespace.
- It achieves this through a combination of a decentralized blockchain, cryptographic proofs, and cryptoeconomic mechanisms.
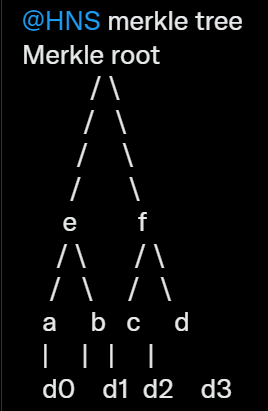
- Merkle Tree in Handshake:
- Handshake uses a Merkle tree based on RFC 6962 (which fixes issues with the Bitcoin Merkle tree) and integrates a padding idea from RFC 7574.
- The Merkle tree is constructed from a list of transactions (such as domain registrations).
- Each transaction is hashed using SHA3-256, resulting in a 32-byte digest.
- These digests become the leaves of the Merkle tree.
- Pairing and Hashing:
- The hashes are paired and concatenated, forming 64-byte chunks.
- Each chunk is hashed again using SHA3-256, producing a new 32-byte digest.
- This process continues until there is only one hash left—the root of the Merkle tree.
- Verification:
- To prove that a transaction is included in the Merkle tree, one needs to provide the path from the transaction hash to the root, along with the sibling hashes at each level.
- The verifier can then recompute the hashes along the path and check if they match the root.
- Compact Verifiable Proofs:
- Handshake ensures compatibility with embedded and mobile devices by using compact verifiable proofs.
- The proof sizes are smaller than base-16 trie proofs and significantly improve performance.
- Decentralized Community Coordination:
- Inspired by the free and open-source software community, Handshake achieves decentralized coordination.
- Ownership of a commodity token by those capable of integrating and using Handshake optimizes for the long-term incentives of the free and open-source community.
In summary, Handshake’s Merkle tree-based approach replaces the social function of centralized corporations with self-interested gift economies, fostering a decentralized and secure internet infrastructure 1.
Feel free to explore Handshake’s whitepaper and technical documentation for more in-depth information! 🌟
learn more: HSD – Merkle Tree
Stay in the NOW with Inner I Network;
